Участник:Dorou/Черновик
The NTOS or Modular Computer feature provides players with a realistic computer system for their Consoles, Laptops, Tablets and PDAs. These can be ugpraded and loaded with a long list of programs to assist with your role, send messages, set up chat rooms and much more.
Computers
Types of Computer
Modular computers come in four types:
- Modular Computers, which can be built or found around the map and usually have the highest capacity and processing power.
- Laptops, which can be acquired from the loadout menu or from computer vendors.
- Tablets, which are similar to laptops but have a smaller information capacity in exchange for not needing to be placed on a table or floor space to use.
- PDAs, which have the smallest capacity but can fit in ID and Belt inventory slots.
Computer Vendor
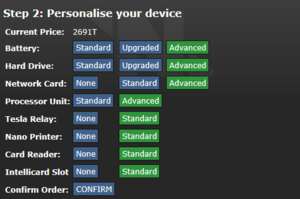
The computer vending machines on D1 and D3 can be used to buy new computers using thaler. You can select the components and quality of parts you want, with a corresponding price tag.
Components
These computers are all modular, which means they consist of various components that can be taken out, replaced and swapped between computers. Data on these components will be available on the new devices, and components like network cards will keep their network addresses.
Parts can be removed using a screwdriver, and placed back inside at will. New parts can be printed with a Protolathe. Modular Computer frames can be built with construction from steel sheets. Laptop and Tablets can be obtained from your loadout menu and the computer vending machines. New PDAs can be acquired from command personnel.
Programs
Installing Programs
To install programs you need to open the NTNet Software Download Tool which will be pre-installed on every hard drive. You will see options depending on your access level and whether or not NTNet is accessible from your location. If it is not accessible, you are either off of the Torch or the telecommunications system is somehow misconfigured or damaged. Downloading programs will take some time depending on your network card. Each program has a certain capacity in units of GQ - Your hard drive size determines how many programs can be installed. Note that this does mean that some programs cannot be installed on the smallest devices. However, you can free up memory using the NTOS File Manager should you need to.
Generic Programs
These programs are available to multiple departments and provide general ship, communication or personal management functions.
- Arcade Games: There are a variety of games available randomly selected each round. Use this to get through the dead periods in each shift!
- Camera Monitoring: Depending on your access level, this program will allow you to see through all the cameras on the ship and through any shuttles within range.
- Computer Configuration Tool: Installed by default on any computer. Allows you to turn various modules in your computer on or off, which can be useful for saving power.
- Crew Records: Lists the crew active in the current shift and allows you to look at their records. If you have certain accesses, you will be able to view and/or edit restricted data such as security and medical records. Can also be used to create new records for Stowaways, refugees, etc.
- Crew Manifest: Lists all active crew, their departments and their roles.
- Deck Management: Allows you to fill out mission and flight plans and post them globally. This is very important to Pilots, Explorers and Miners especially.
- Docking Control: Allows you to see the status of the ship's docking ports, their docking access codes, and undock docked ships.
- Email Client: In your character's notes you will have an email login and password. You can use these with this program to send email to anyone else with an email address.
- Library: Lets you access the persistent library and download books to read from it.
- NanoWord: A word processor program with many formatting options, allows you to save and print documents.
- NTOS File Manager: Can be used to delete files and programs, view log files and txt files.
- NTNet/ExoNet News Browser: View and download news articles from NTNet, which may contain important lore news to the setting.
- NTNet Software Download Tool: Allows downloading of new programs. If your computer has been emagged then it will display additional options.
- NTNet Relay Chat Client: Allows creating chatrooms that can be joined by other people anonymously, with a password and moderated.
- NTNet P2P Transfer Client: Allows transfer of files between computers over the network.
- Report Editor: Contains some pre-configured templates for common paperwork needs.
- Scanner: This program interfaces with your paper scanner module to scan text and photos.
- Supply Management: Allows you to place orders with supply, and if you have the required access, to control the supply shuttle and approve/deny orders.
Command Programs
- ID Card Modification Program: Usually used by the XO, this can allow editing an inserted ID card's access to add any accesses that are on the user's ID card to it. Or modify the name, terminate that person, etc.
- Command and Communications Program: Facilitates important command-level options, such as contacting EXO command, setting the alert level, opening the saferooms and more.
Engineering Programs
- AI Maintenance Utility: Allows viewing and resetting of the inserted AI IntellicardCard's laws.
- Alarm Monitor: All currently active alarms across the ship will be visible here. Useful for damage control.
- Atmospherics Control: Allows for remote control of air alarms.
- Email Administration Utility: Allows the Chief Engineer to handle email administration and monitoring tasks.
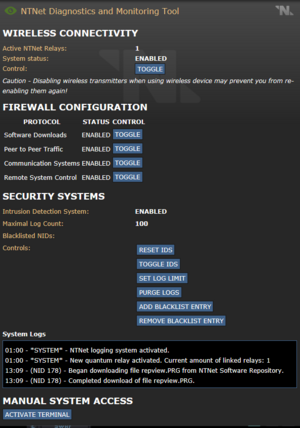
- NTNet Diagnostics and Monitoring: Allows the Chief Engineer to monitor all NTNet traffic, such as downloads of programs and the NIDs of the computers that are doing this. Allows control over the NTNet system's state, turning it on and off, toggling security features, log length, etc.
- Power Monitor: Allows you to monitor power usage across all areas of the ship, and power generation.
- RCON Remote Control: Allows you to control the SMES across the ship, and enable the deck bypass systems.
- Shield Generators Monitoring: Allows you to view, but not adjust, the settings and state of all shields across the ship.
- Supermatter Monitoring: Allows you to monitor important readouts from the Supermatter chamber, such as the EER, temperature and atmospheric composition of the reactor chamber.
Medical Programs
- Suit Sensors Monitoring: Gives you information on all crew that have their suit sensors turned on, depending on the level they have it set to. Very useful for hunting down wounded people. If you keep this program open on a tablet in your pocket, it will flash red when someone is hurt.
Security Programs
- Warrant Assistant: Allows creation, modification and viewing of warrants.
- Use of Force Authorization Manager: Allows you to allow/deny kill settings on weaponry, as well as see who has swiped their ID cards in their weapons and where the weapons are located.
Antagonist Programs
Downloading and using these programs will result in alarms being raised by the NTNet Diagnostics and Monitoring program. Methods for dealing with this, and countermeasures to these methods will be discussed later in this guide. Unlocking these programs in the download tool is done by using an emag on the computer. These programs tend to be very large and cannot be installed on PDAs.
- Camera Decryption Tool: Allows you to access camera feeds without having the required access.
- DDoS Traffic Generator: Allows you to force NTNet to shutdown until restarted by Engineering personnel, preventing many computing tasks from being possible such as tracing your computer, downloading new programs, etc. This program targets an NTNet Quantum Relay, of which there is one at the start of the round. More can be built to make the system more resistant. To fix NTNet after a DDoS, you must physically go to the relay and reset it.
- NTNet Access Decrypter: Allows you to add accesses to the inserted ID card. This takes a significant amount of time to complete per access.
- Revelation: This virus can be used to destroy the hard drive of the computer it is installed on. Can be useful for covering your tracks.
- TaxQuickly 1.45b: This program comes pre-installed on many character's PDAs. For traitors that chose the PDA Uplink option it will allow you to spend your telecrystals for items. For non-antagonists this does nothing.
Using NTNet Diagnostics and Monitoring
This program is important for the Chief Engineer to understand. It provides many options for administrating and monitoring the NTNet activity aboard the ship.
- Control Toggle: If someone is using a wireless computer to mess with the NTNet diagnostics program, you can shut them out by toggling this. Only computers with wired network cards will be able to use the program, forcing your adversary to be much less mobile.
- Software Downloads Toggle: Stops all downloads of new software for everyone on the ship.
- Peer to Peer Traffic: Toggle to prevent all P2P traffic via the NTNet P2P Transfer Client.
- Communication Systems: Toggle to prevent all instant messaging via the NTNet Relay Chat Client.
- Remote System Control: Toggle to prevent remote control of RCON, Air Alarms, etc.
- Reset IDS: Turns off the IDS (Intrusion Detection System) alarm. This system detects antagonist program actions.
- Toggle IDS: Toggles the IDS system.
- Set Log Limit: Sets the max log limit between 10-500.
- Purge Logs: Deletes logs. Will display a message saying they were deleted.
- Add Blacklist Entry: Provide an NID to prevent it from accessing any network functions.
- Remove Blacklist Entry: Remove an NID from blacklist.
- System Logs: Logs all setting changes, all downloads, DDoS attacks, and NIDs of the responsible network cards.
- Activate Terminal: Opens a terminal, same as Alt+Ctrl+Clicking a computer.
Using the Terminal
Depending on your Information Technology skill, the terminal will give you access to a list of commands that allow you to manipulate and gain information about your computer and NTNet. If you have the required access, it can allow useful features such as finding the physical location of an NID, and creating proxy links between computers to hide yourself. To access the terminal on a modular computer, Alt+Ctrl+Click on the computer. You can type 'man' in the terminal to find the commands you have access to, and 'man <command>' to find some information on how to use each command.
| Command | Description |
|---|---|
| exit | Closes the terminal. Requires basic Information Technology. |
| banned | Lists the currently banned NIDs on the network. This is useful for detecting whether your proxy devices have been stopped physically or remotely. This requires network access. |
| ifconfig | Returns information about the network adapter on this computer, listing the real and visible (proxy) NIDs. |
| hwinfo | Lists the currently installed hardware in this computer. Usefully, this can help you work out what kind of device a machine is once you've ssh'd into it – Look at the network card type for a start! |
| locate | Tells you the location of the specified NID, it will list the area the NID is in. Requires master Information Technology. This requires network access. |
| relays | Provides the number of currently active NTNet Quantum Relays on the network. This is important for finding how resistant a network is to DDoS attacks, you will need to DDoS each relay separately. |
| ping | Tells you if a given NID is reachable or not. Useful for working out if a network card has been removed/destroyed/offlined. |
| proxy | When provided with 'proxy -s <NID>' this will route all traffic so it appears to NTNet to come from <NID>. This is extremely useful for antagonists for hiding their tracks. Multiple proxies can be chained together.
When a proxy is created, the target machine creates a log file called 'proxy', which lists the NID of the machine it is being proxy'd into from. If you are trying to follow a proxy-chain, this is the only way of determining the next link, which you can then blacklist or locate. |
| ssh | Opens a terminal on the target NID, allowing you to use all these commands as if you were using that machine. This requires network access. |
| status | Lists the current status of the NTNet Intrusion Detection System and NTNet itself. This requires network access. |